|
|
< Day Day Up > |
|
Hack 27 Tunnel Your IRC Connection with SSH
Encrypt your conversation and access IRC servers through firewalls using SSH. Firewalls are a fact of life these days, and if you want to connect to a private IRC server via the Internet, chances are you're going to have to deal with one. Many firewalls block IRC but allow SSH connections. This hack explains how to take advantage of this fact to tunnel your IRC connection via SSH and bypass the firewall. Unsurprisingly, you will need an SSH client to use SSH. If you run Linux/Unix, then you almost certainly already have an SSH client installed or can easily obtain it from the provider of your operating system. If you use Windows, a number of SSH clients are available. The most popular seems to be PuTTY, which is free and can be downloaded from http://www.chiark.greenend.org.uk/~sgtatham/putty. This hack contains instructions for both PuTTY and OpenSSH. You will also need an account on an SSH-accessible machine on the same side of the firewall as the IRC server (perhaps the IRC server itself). The concept of tunneling is quite simple. The SSH client listens on a port of your choosing on the client machine and forwards everything via the encrypted link to the SSH server. This then passes everything on to a remote machine and port also of your choosing. An additional advantage of tunneling your connection with SSH is that your IRC session is encrypted and thus concealed from prying eyes between the two end-points of the SSH tunnel. 4.12.1 Setting Up an SSH Tunnel with OpenSSHOnce you can log into the SSH server, creating the tunnel is as simple as adding an extra command-line parameter to ssh. For example, let's say that your IRC server is called irc.example.com and runs IRC on port 6667, and your SSH server is ssh.example.com. The command to connect to the SSH server and set up the tunnel will be: % ssh -L 6030: irc.example.com :6667 username @ ssh.example.com This example uses 6030 as the port at the local end of the tunnel, but it could be any port you like. If you use a privileged port number between 0 and 1023, you will have to run ssh as root. It is usually easier (and safer) to simply choose any unused port from 1024 to 65534. To connect to the IRC server via the tunnel, tell your IRC client that its server is localhost, port 6030. The IRC client will then connect to the local end of the IRC tunnel, which will forward the data to the other end. To avoid having to type in the whole command every time, you can add a section to your SSH configuration file that will establish the tunnel every time you connect to the SSH server. Open (or create) the file ~/.ssh/config and add the following lines to the end: Host irc HostName ssh.example.com LocalForward 6030 irc.example.com:6667 User username Now you need only run ssh irc to connect to the SSH server and establish the tunnel. Note that the domain name you should use for the IRC server is its internal name. In many cases, this may just be the unqualified name of the server, which in the case of irc.example.com would be irc. 4.12.2 Setting Up an SSH Tunnel with PuTTYPuTTY works in terms of
sessions, which contain all the configuration
details for a connection to a particular SSH server. To add tunneling
of IRC connections to an existing PuTTY session, launch PuTTY and
load the saved session. Select the Connection Figure 4-28. Enabling IRC tunneling in PuTTY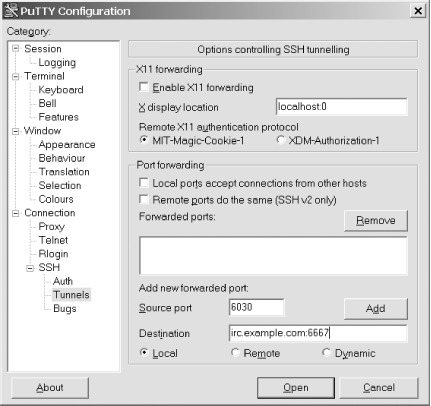 4.12.3 Allowing Third Parties to Bypass the FirewallMost SSH clients that support port forwarding also allow the user to permit IRC clients running on any machine to use the tunnel and bypass the firewall. In OpenSSH, you can do this by adding the -g command-line option. This can be useful in some situations (for example, allowing all staff in a small branch office to access a server at the company headquarters), but you should be aware that if the SSH client machine is not behind a firewall, then anyone on the Internet can connect to the hitherto private IRC server. You should always check with your network administrator before enabling third-party access. —Steve Jolly |
|
|
< Day Day Up > |
|