1.3 LDAP Models
LDAP
models represent the services provided by a server, as seen by a
client. They are abstract models that describe the various facets of
an LDAP directory. RFC 2251 divides an LDAP directory into two
components: the protocol model and the data model. However, in
Understanding and Deploying LDAP Directory
Services, by Timothy A. Howes, Mark C. Smith, and Gordon
S. Good (MacMillan), four models are defined:
- Information model
-
The information model provides the structures and data types
necessary for building an LDAP directory tree. An entry is the basic
unit in an LDAP directory. You can visualize an entry as either an
interior or exterior node in the Directory Information Tree (DIT). An
entry contains information about an instance of one or more
objectClasses. These
objectClasses have certain required or optional
attributes. Attribute types have defined encoding and matching rules
that govern such things as the type of data the attribute can hold
and how to compare this data during a search. This information model
will be covered extensively in the next chapter when we examine LDAP
schema.
- Naming model
-
The naming model defines how entries and data in the DIT are uniquely
referenced. Each entry has an attribute that is unique among all
siblings of a single parent. This unique attribute is called the
relative distinguished name (RDN). You can uniquely identify any
entry within a directory by following the RDNs of all the entries in
the path from the desired node to the root of the tree. This string
created by combining RDNs to form a unique name is called the
node's distinguished name (DN).
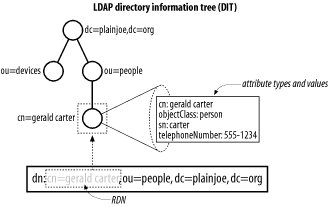
In Figure 1-4, the directory entry outlined in the
dashed square has an RDN of cn=gerald carter. Note
that the attribute name as well as the value are included in the RDN.
The DN for this node would be cn=gerald
carter,ou=people, dc=plainjoe,dc=org.
- Functional model
-
The functional model is the LDAP protocol itself. This protocol
provides the means for accessing the data in the directory tree.
Access is implemented by authentication operations (bindings), query
operations (searches and reads), and update operations (writes).
- Security model
-
The security model provides a mechanism for clients to prove their
identity (authentication) and for the server to control an
authenticated client's access to data
(authorization). LDAPv3 provides several authentication methods not
available in previous protocol versions. Some features, such as
access control lists, have not been standardized yet, leaving vendors
to their own devices.
At this high level, LDAP is relatively simple. It is a protocol for
building highly distributed directories. In the next chapter, we will
examine certain LDAP concepts such as schemas, referrals, and
replication in much more depth.

|
