4.1 Overview
4.2 Design Overview
4.3 Receiving Network Data
4.4 Runtime Flags
4.5 Configuration
4.6 Experiments with Honeyd
4.7 Services
4.8 Logging
4.9 Summary
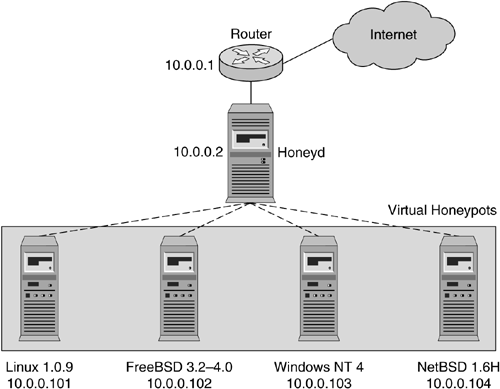
Honeyd is a framework to instrument thousands of Internet addresses with virtual honeypots and corresponding network services. Usually, we configure Honeyd to instrument-unallocated IP addresses on an existing network. For each IP address, we can tell Honeyd how we want the simulated computer to behave. For example, we could set up a virtual web server that seems to run Linux and listens on port 80. We could create a virtual honeypot on another IP address with a network stack that looks like Windows on which all TCP ports seem to be running services. This would allow us to receive the first TCP payloads for worms or probes. Honeyd can be used to set up a few decoys in an existing network or to create routing topologies consisting of hundreds of networks and thousands of hosts with just a single computer. This chapter describes in detail how Honeyd works, how it can be configured, and how to deploy it.
Your first honeypot is going to be an exciting experience. You are going to watch its logs for hours, waiting for interesting traffic, for remote attacks to probe it, and, finally, for someone to break into it. Unfortunately, when using only a single IP address, this can take a while. However, there are alternatives that can increase your exposure on the Internet dramatically. Clearly, if it takes a long time for a single address to be probed and attacked, it might take less time to observe interesting activity if you are watching a hundred, or maybe a thousand, IP addresses.
This is where Honeyd comes into play. It is a low-interaction virtual honeypot framework that can create thousands of virtual honeypots on a single network or even all over the Internet. Honeyd supports the IP protocol suites [92] and responds to network requests for its virtual honeypots according to the services that are configured for each virtual honeypot. When sending a response packet, Honeyd's personality engine makes it match the network behavior of the configured operating system personality. It is available as an open source software released under the GNU Public License (GPL) and runs on most operating systems.
Not only can Honeyd leverage unallocated network addresses to give you more insight on malicious activity on the Internet, but it can also be used to deter adversaries from attacking your real systems. A good example is the annual Cyberdefense exercise, a competition between the US military academies and red teams from the National Security Agency (NSA). Each academy has a team of students tasked to protect their networks and the red teams try to break into them or create other kinds of havoc. A few years ago, when Honeyd was first released, some students beefed up their networks by configuring Honeyd to create a few hundred virtual honeypots. These honeypots were meant to deter only the adversaries and keep them from attacking the real machines. This strategy was suprisingly successful, and the students enjoyed watching the NSA teams trying for hours to break into machines that did not really exist.
Similarly, we can use Honeyd to confound and confuse attackers all over the Internet. While this chapter equips you with the basics on how to deploy Honeyd, following chapters explain how to snare spammers, build your own systems to capture millions of spam e-mails, and even how to capture worms. So stay tuned!
Honeyd has many interesting features:
Simulates thousands of virtual hosts at the same time: The main reason for using Honeyd is its ability to create thousands of virtual honeypots at the same time. An adversary can interact with every single host via the network and experience different behavior from each host depending on how it has been configured.
Configuration of arbitrary services via configuration file: You can provide arbitrary programs that interact with an adversary. Whenever Honeyd receives a new network connection, it will start the program that you have specified for this connection to talk back to the attacker. Instead of running programs, you could also use Honeyd to proxy connections to other machines or use features like passive fingerprinting to identify remote hosts and random sampling for load scaling.
Simulates operating systems at TCP/IP stack level: This feature allows Honeyd to deceive Nmap and Xprobe into believing a virtual honeypot is running any configured operating system. To further increase realism, the policies for treating fragment reassembly and FIN-scanning can be adjusted as well.
Simulation of arbitrary routing topologies: The routing topologies can be arbitrarily complex. It is possible to configure latency, packet loss, and bandwidth characteristics. Honeyd supports asymetric routing, integration of physical machines into a virtual topology, and distributed operations via GRE tunnels.
Subsystem virtualization: With subsystems, Honeyd can execute real Unix applications under the virtual name space of a honeypot, — for example, web servers, ftp servers, and so on. This feature also allows for dynamic port binding in the virtual address space and background initiation of network connections.
Before you can experiment with Honeyd and try its various features, you need to install it on your computer. We hope that you are running an operating system like Linux, Mac OS X, or FreeBSD because Windows[1] does not really offer the flexibility of a Unix system. If you are running Debian, you can simply install the Honeyd package as root with
[1] The adventurous Mike Davis went forth and ported an older version of Honeyd to Windows. You can download it from www.securityprofiling.com/honeyd/honeyd.shtml. However, be warned that the Windows binary does not support many of the advanced features of the Unix version.
apt-get install honeyd
On the other hand, if you like to live on the cutting edge and do not mind compiling software, you can always get the source code yourself and compile the latest and greatest. The following steps will get you up and running:
1. | Make sure that you have all dependencies installed. Honeyd requires libevent, libdnet, and libpcap. You can download the latest version of libevent from www.monkey.org/~provos/libevent/; libdnet lives at libdnet.sourceforge.net/, and libpcap can be downloaded from www.tcpdump.org/. |
2. | Extract the source packages with tar -xzf <package>.tar.gz. |
3. | For each package, enter the package directory and then execute ./configure, make and sudo make install. |
4. | Find and download the latest release of Honeyd from www.honeyd.org/release.php. If you have gpg installed, you should also download the digital signature and verify the integrity of the Honeyd package. |
5. | Extract Honeyd with tar -xzf honeyd-<version>.tar.gz. |
6. | Configure the package by entering the source directory and executing ./configure. The configure script might fail if you do not have the Python development libraries installed. You can either install them, which will allow you to make use of some interesting scripting features and Honeyd's internal web server, or you can decide to skip the Python capabilities by executing ./configure --without-python If you are still unsuccessful you might want to consult the frequently asked questions at www.honeyd.org/faq.php. |
7. | Compile the binary with make, and then install it with sudo make install. If you do not have sudo installed, then execute the command after becoming root. |
The binary should now be installed. Before we can try to run Honeyd with one of the provided configuration files, you must configure your host so that it does not forward IP packets. On Linux, this can be achieved by
echo 0 > /proc/sys/net/ipv4/ip_forward
On a BSD system, the systctl command can be used to turn IP forwarding off:
sysctl -w net.inet.ip.forwarding=0
With IP forwarding enabled, the operating system kernel would try to forward any IP packet that it receives for any of the virtual honeypots. This can lead to horrible packet duplications and even packet storms. An alternative that does not require disabling IP forwarding is configuring a firewall on the Honeyd host to block all packets sent to the honeypots. Honeyd will still be able to respond to them, but the operating system itself is going to ignore them.
If everything went all right, Honeyd should be up and running now. However, before we will talk about configuring the daemon, a brief discussion of the overall design and its limitations is required to really understand what is going on.