|
|
< Day Day Up > |
|
10.3 Accessing the ACID ConsoleThe ACID web page should be fully functional on the network intrusion detection system. This page is normally accessible using the following URL in a graphical web browser. Remember when accessing this page as administrator or as the primary Snort user, all rights and privileges to modify the snort database are granted. Use the following URL for modifying database content.
To view ACID web content without the rights to modify or delete entries, open the acidviewer web page. Verify the MySQL database permissions are set correctly so that any user referencing this particular page cannot remove or hide alerts.
This page should be available only to those individuals needing to consult or view logged alerts. These users should not have the authority to remove existing alerts. Employees should not be able to transmit malicious or harmful content through your network and then cover their tracks once the IDS or internal sensor detects their packets. Likewise, no one outside your network should have access to either of these pages. The content within the ACID web pages displays source and destination IP addresses containing internal IP addresses. If you are running Name Address Translation (NAT) on your internal network, this information could provide an attacker the added advantage of knowing not only your numbering scheme, but what boxes might be vulnerable and what ports on these machines may be open to attack. I highly recommend password-protecting these and all other web pages of a sensitive nature. Even most internal network end users should not be authorized to view the ACID web pages. 10.3.1 Using ACIDAfter resolving most security concerns regarding ACID's use and Internet accessibility, begin examining the component parts of the ACID web page and analyzing what each link does. The ACID page, overall, is self-explanatory, although understanding where each hypertext link leads helps in determining the types of packets being captured. Starting with the main ACID page, this section examines each link, explains where it leads, and discusses how to interpret the content. 10.3.1.1 Main ACID pageThe main ACID interface (as shown in Figure 10-3) provides numerous links that explain, in detail, each separate element captured by Snort. This page greets visitors to the typical ACID site. It conveys most pertinent information at a glance. Figure 10-3. ACID's main interface (each link is highlighted)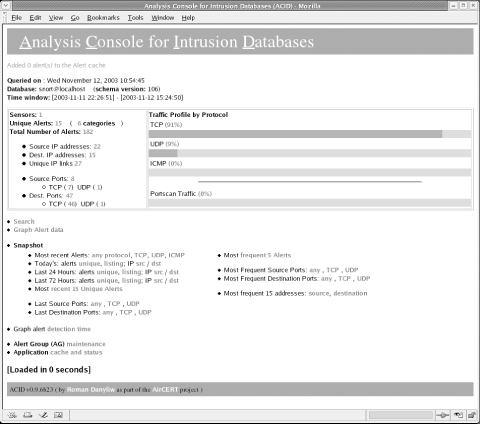 This page provides a brief summary of the primary links and lists the alerts registered by Snort. The information listed on the very first line (in red) notifies the visitor of new alerts added to the cache since the page was last viewed or refreshed. Remember, this is the alert cache found in the /var/log/snort directory. This file constantly updates as Snort detects new packets. The web page also refreshes itself periodically if left open, providing an up-to-the-minute analysis of what is happening on your system. The next three lines on the main ACID web interface display the following information: first, the current timestamp or when the database was last queried via the web interface; second, the database name—or, in this case, the username—by which Snort accesses the MySQL database; and third, the time window, or when the Snort process was first started until the present time. As shown in the initial screenshot, the following alerts were logged over the space of five days. The last item of information, the time window, is useful for security administrators who need to know the overall logging period at a glance. 10.3.1.2 Alert informationThe next section of the ACID web interface is set apart by two individual frames that break down the database into easily digestible chunks. The right-hand frame graphically displays the protocol traffic in percentages. It also shows any and all portscan traffic detected by Snort. Portscans are relatively frequent occurrences, and knowing what percentage of the events of interest are actually scans from outside entities is useful for determining if your network has become a target for an attack. The frequency and source of a portscan can be indicative of forthcoming events. Beware of falling into the "false positive" lull and ignoring the seriousness of portscans. You will have to determine for yourself what percentage of portscan traffic should be considered normal and what may constitute early warning signs of an attack. While you don't want to investigate every portscan, a sudden increase in the number of portscans is a cause for concern. The left-hand frame shows the number of sensors capturing data, the number of unique alerts and their respective categories, along with the total number of alerts. The categories selection is another name for the alert classification in question. These fall under the rules selection within Snort. The alerts are next broken down by their source and destination addresses. The unique IP links are distinct connections established from a specific source address to a destination address. They determine what IP address or machine name the source address is targeting. This detail is useful for identifying the flow of traffic—whether the packet is destined for an internal host or is an outbound packet. Below these categories are the source and destination ports. Each number on the first line specifies the originating unique port number and then is separated into TCP or UDP packets. The same applies to the destination ports. A security administrator can return to her logs to confirm if the packet was crafted to originate at a higher or lower port than normally intended. Each number shown in these sections is a hypertext link to more descriptive pages. These pages list the infraction or alert type, the IP addresses, and the port numbers in greater detail. It is worthwhile to click on each of these links and view the contents collected under the respective pages. 10.3.1.3 Searching and graphingBelow the framed section is the interactive portion of the ACID web page. Inquiries to the Snort database for a particular signature or packet matching the criteria specified are made via a link to the Search function. The Search link is for viewing and reading through the packet payload of any offending alert stored within the logs. Unlike most other commercial intrusion detection systems, ACID, together with MySQL and Snort, captures and stores packet payload data. Even when the system alerts you to a possible intrusion, you don't need to trust it implicitly. You can go back and verify that the payload matches the signature of a valid attack. More will be said about the Search capabilities of ACID later in this chapter. This is a key function towards the elimination of false positives for user-created rules. Below the Search option is the Graph Alert Data link. Here it becomes important to properly compile GD into PHP and install JpGraph. These applications generate a real-time graph that displays the types and amounts of alerts detected. The graph itself is customizable in various ways and the data it examines can also be modified to suit. This link is examined in more detail later in this chapter. Both the Search and the Graph Alert data hyperlinks bring up pages in which the typical user or security administrator can input more information and query the MySQL database. Knowing both these pages render data to the user is important for understanding the types of packets logged by Snort. 10.3.1.4 Data snapshotsThe next section on the main ACID page is labeled Snapshot. The links here provide a quick look into the most recent alerts over varying periods of time or by frequency or address or port. The links themselves are relatively self-explanatory and are useful if you are familiar with the types of attack or the port numbers or addresses of the systems in question. Each link provides a detailed glimpse of what is currently happening on the network. Next is Graph alert detection time, which links to yet another graph-generating chart, and allows users to view the time alerts are logged. This section is helpful when attempting to determine the times at which most alerts were detected and if additional security measures should be implemented at different times of the day. The final two links are for advanced customization or knowledge gathering. The first, Alert Group (AG) maintenance, allows users to create and modify their own alert groups. Snort can create additional alert groups, aside from the basic alert file. For example, if you want all ICMP packets to be logged on a particular system, create a new Alert Group and give it a descriptive name. This name is intended mostly for informational purposes. It can be useful on large networks to group signatures related to a single event (or group of related events). It can also be useful because it allows multiple security administrators to understand what is going on during an incident. The item listed below the Alert Group maintenance link provides information regarding the Application cache and status of MySQL or the database of your choosing. This link displays a page with details regarding the installed PHP version and its compatibility with the IDS system and related applications. It also generates information about the database type and the events stored within the Alert and IP Address cache. |
|
|
< Day Day Up > |
|