In addition to the special terminal server tool described in the previous section, several standard tools have been adapted to the multiuser environment. Table 4.2 offers you a quick overview. The tools that are executed from a remote computer over the network are labeled accordingly.
|
Tool |
Specific Function |
Remote Execution |
|---|---|---|
|
Task Manager |
Display of process allocation of user accounts under the Processes tab. Shows all current user sessions under the User tab. |
No |
|
System Monitor |
Additional objects for monitoring a terminal server. |
Yes |
|
Event Viewer |
Additional event sources. |
Yes |
|
Control Panel |
For setting of specific system properties and custom installation of applications. |
No |
Right-click the desktop taskbar, and select Task Manager from the menu. You can alternatively invoke the Task Manager from the security screen. The first tab of the main window displays all programs currently running for the logged-on user and their status. If a programs stops responding, you can remove it from memory using the End Task button. This tab is not especially important to terminal server administrators, whose interest lies more in the current programs and processes of other users.
The Processes tab gives you a more detailed look at current processes as well as Windows services. This tab is unique because it lets you see who is using which process, providing you a differentiated perspective of system activity. An administrator can see all the current system processes if the Show processes from all users option is checked. All other users see only their own processes.
The memory requirements of the individual application processes are of particular interest to terminal server administrators. It is easy to see that different instances of the same application can have very different memory requirements. For example, Figure 4-9 shows this quite clearly for Explorer.exe, the process responsible for managing windows during a user session.
You can right-click one of the processes to set its priority level (low, below normal, normal, above normal, high, or real-time). However, changing the priority level of a process can produce unwanted side effects in terms of system stability and process response times. Thorough testing is recommended before you change a priority level.
| Tip |
You can start a process at High using the Start/high <Program Name> command. The other priority levels are available using the /low, /belownormal, /normal, /abovenormal, or /realtime arguments. However, use the /realtime argument only with the utmost caution. |
The Performance tab displays the utilization of all physical or virtual processors (supplied by hyperthreading), swap-file utilization, and detailed information on memory usage. Unlike an administrator, users cannot see all the available memory. They see only the amount of memory that is allocated to their current sessions. The most important information in this tab for terminal server administrators is total physical memory versus available physical memory. Terminal servers tend to experience abrupt performance bottlenecks when they are very low on physical memory. This happens whenever the current reserved memory (that is, the virtual memory used) significantly exceeds existing physical memory.
The Windows Server 2003 Task Manager has another two tabs beyond those in Windows 2000. One is the Network tab, which allows you to observe the network load, the transmission rate, and the status of available network adapters. You can verify in this tab that the required network bandwidth is not pushed to its limits. For instance, an Ethernet network adapter should not constantly exceed 30 percent to 50 percent capacity.
The second tab is Users, and like Terminal Services Manager, it displays the user name, the session ID, the status, and the session name of each user session. Task Manager is therefore an excellent tool for gaining a general overview of a terminal server’s utilization.
Another essential administration and analysis tool included in Windows Server 2003 is the System Monitor. It displays available and used system resources, which Windows Server 2003 manages with internal counter variables. This tool helps you identify system bottlenecks and trace results during manual system optimization.
There are three types of performance indicators or counters in System Monitor:
Instantaneous counters which display the most recent measurement.
Average counters which measure the value over time and display the average value of the last two measurements.
Difference counters which subtract the last measured value from the previous one and display the difference.
Using counters, the System Monitor oversees the entire system and the network. With the proper permissions, you can also access remote computers. Practically all data measurable at run time can be recorded and displayed as a counter. The data can be processed in several ways.
Collect and display real-time performance data for a local or several remote computers. Display current or previous data recorded in a performance log.
Present data in a printable diagram, histogram, or report view.
Create reusable performance-monitoring configurations that can be applied to other computers running Microsoft Management Console.
The System Monitor thus supports manual, demand-driven, and automatic sampling at predefined intervals. You can select the start and end times to display log data for a certain period of time.
The System Monitor offers an overwhelming array of options for displaying local and remote system information. Administrators have any number of ways to approach system analyses on a local or remote computer under Windows Server 2003.
The following are the most important counters that can point to a performance bottleneck in a terminal server:
Network interface—Total Number of Bytes/s: The rate at which bytes are sent and received over the interface If this value approaches the physically available network bandwidth, the network should be segmented and/or an additional network card installed.
Processor—%Processor Time Percent processor time needed to execute a non-idle thread. This performance measure is the primary indicator of processor activity. The time span that the processor needs to execute the idle-process thread in each sampling interval is subtracted from 100 percent. Each processor has an idle thread that consumes cycles during which no other threads can be executed. The performance indicator shows the average consumption during the sampling interval in percent by subtracting the time the service was inactive from 100 percent. If the processor time value is consistently high (more than 80 percent) while the network load is low, the processor is too weak.
Processor—Interrupts/s The number of hardware interrupts that the processor receives and processes per second. This value is an indirect indicator of the activity of devices that generate interrupts, such as the system clock, mouse, disk drivers, network cards, and other peripherals. These devices usually generate a processor interrupt when they finish a process or require intervention because normal thread execution is suspended during the interrupt. This performance indicator shows the difference between the values of the last two sampling intervals divided by interval duration. If this value is high (more than70 percent) for an extended period, a network card might be receiving faulty network packages.
PhysicalDisk—%Disk Time The percentage of time needed by the selected drive to process read and write requests. If this value is consistently high (more than 25 percent), the access speed of the hard-drive system is insufficient. In this case, you might want to consider using RAID systems with ample cache memory.
Redirector—Server Sessions The number of security objects that the redirector manages. A large number of these objects on terminal servers is often an indication of how frequently user sessions access file server shares (for example, home folders). Above-normal values for this indicator in conjunction with terminal server bottlenecks often point to the problem. Usually, reducing the number of connected drives per user session improves the situation.
Server Work Queues—Queue Length The current length of the server queue for this CPU. A sustained queue length significantly above four indicates processor overload. This is an instantaneous value, not an average count over time.
Memory—Available Bytes Physical memory available for processes (in bytes). This value is calculated by adding up zeroed, free, and standby memory. Free memory is available memory. Zeroed memory consists of memory pages filled with zeros. This type of memory prevents subsequent processes from accessing data of previous processes. Standby memory is memory that is still available but has been removed from the working pages of the process. This indicator shows only the last measured value, not an average. If you constantly have little free memory in relation to entire memory, the physical memory is undersized. System performance suffers significantly in this case.
Memory—Committed Bytes Committed virtual memory in bytes. Committed virtual memory is physical memory for which memory space is reserved in the swap file so that it can be rewritten to the data carrier. This indicator shows only the last measured value, not an average. If its value approximates the available physical memory, the system begins a lot of read/write operations, resulting in significantly reduced performance. The solution is to add memory to the system.
System—Processes The number of system processes at the time of data collection. This is an instantaneous indicator, not an average over time. Each process represents the execution of a program.
System—Processor Queue Length The number of threads in the processor queue. Even if you have several processors, there is only one queue for processor time. This performance indicator counts only finished threads, not threads being executed. If this value is consistently higher than 10 threads per available processor, the processors are overloaded. If this value is significantly higher than 20 threads per processor, you definitely have a bottleneck. This indicator shows the last measured value only, not an average.
A terminal server provides additional performance indicators offering specific types of analysis.
Terminal Services A specific System Monitor object with three performance indicators for active and inactive sessions and for the total number of sessions.
Terminal Services Session A specific System Monitor object with some 100 performance indicators for the RDP protocol, processor load, necessary memory resources, input and output buffer, compression, swapping activity, error rate, caching behavior, and asynchronous communication. Each user session can be monitored and analyzed individually.
When you start System Monitor, it is displayed as a snap-in on the Microsoft Management Console, like so many other tools in Windows Server 2003. The Performance logs and alerts option lets you automatically record performance data of local or remote computers. The System Monitor can display the performance data that was logged. As an alternative, you can export the results to spreadsheet programs or databases to generate reports or analyze the data. This is a good option for regular long-term analysis of the performance indicators listed in the preceding section in a terminal server environment (much like a long-term ECG).
Performance logs and alerts provide the following functions:
Data is recorded in a comma-delimited or tab-delimited format for easy export to spreadsheet programs. In addition, a binary log file format is used for continuous logging, where new data overwrites old.
You can display the data recorded in performance logs and alerts both during and after the recording process.
Because logging is performed as a service (SysmonLog service with the display name Performance logs and alerts, Smlogsvc.exe), data is collected regardless of whether a user is logged on or not.
You can define start and end times, file names and sizes, and other parameters for automatic log creation.
You can define an alert that sends a message, executes a program, or starts a log if the performance indicator value exceeds or drops below a certain setting.
The Event Viewer allows you to monitor Windows Server 2003 events. It replaces the windows that display administrative message to users, who normally have no idea what to do with them. The messages contain information on system events and are therefore more interesting to administrators. A special system service saves these messages as logs.
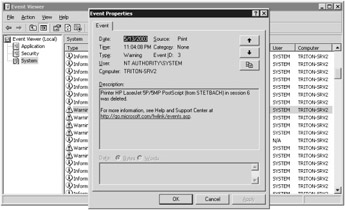
The event log service records three types of logs:
Application The application log contains events recorded by applications or programs. A database, for instance, could record a file error in the application log. The program developer decides which events will be recorded.
Security The security log contains events dealing with security, such as valid and invalid logon attempts, and events involving resource use, such as creating, opening, or deleting files. The administrator decides which events will be recorded in the security log. If the security log option is enabled, you can record all system logon attempts, for example.
System The system log contains events that were recorded by Windows Server 2003 system components. For instance, failure to load a device driver or other system component on startup is recorded in the system log. The types of events that can be recorded are determined by the system components used.
| Note |
All users can view the application and system logs. However, only administrators can access the security log. |
Creating security logs is enabled by default only for the most important options. You can change this setting under the local security settings or Group Policies (as discussed later in this chapter).
The administrator can also set the audit policy for the Event Viewer to stop the system when the security log size is exceeded.
The Event Viewer displays the following events:
Error A major problem, such as data loss or function failure. This error is logged if, for example, a required service was unable to load on system startup.
Warning An event that is not necessarily major but could indicate future problems. A warning is recorded if there is little memory available on the hard drive, a user-session printer is deleted, or there is no license server in the network environment.
Information An event that reports the successful execution of an application, a driver, or a service. An example of an information event is if remote control of a user session on this computer has been requested or if the terminal server cannot assign a client license.
Success Audit A successful, audited security access. If, for instance, a user logs on to the system, it is recorded as a success audit event.
Failure Audit A failed, audited security access. If, for example, a user fails to access a network drive, it is recorded as a failure audit event.
The main Event Viewer window displays the following data for the selected log category:
Type Classification of the event by Windows Server 2003 (error, warning, information, success audit, or failure audit). An icon at the beginning of the event line marks this data.
Date System date when the event was generated.
Time System time when the event was generated.
Source The software component that produced the event (for example, TermService).
Category Classification of the event by the source.
Event Number identifying the event (for example, 1004 for TermService information or 1027 for a TermService warning).
User Identification of the user at the time the event occurred.
A terminal server logs some very specific events, most of which relate to the runtime system, security settings, and licensing. The following is a list of some basic log entries that might appear in the Event Viewer and require action by the system administrator:
The terminal server could not assign a client license.
No license server that can assign valid terminal server licenses was found in the working group or domain.
The connection to a local printer was set up or removed within a user session.
A tool requires Terminal Services to function.
Terminal Services was unable to authenticate a user because the user does not have the required permissions or Terminal Services is no longer running.
An error occurred on setting up a new connection type that requires a unique combination of communication protocol, transport protocol, and network adapter.
Changes currently being made to the registry cannot be applied for the current user. All users must be logged off.
Registry settings could not be saved in the user profile because they have just been changed by another program or service.
The Connect To Another Computer... context menu item with Event Viewer (local) activated allows you to call up log information of other systems on the network running Windows Server 2003. This is very practical, especially when a user reports that the system is unstable and the administrator wishes to make an initial diagnosis remotely.
Filter functions help if the log volume becomes too large for a targeted analysis of certain events. Activate the corresponding dialog box via the Properties menu item of the selected log and use the Filter tab.
You can archive, analyze, and process the logs in files. Corporate policy often requires storage of log information. Stored log files help reconstruct security violations after the fact.
If logs are to be saved frequently, data must not be lost: select the appropriate log-size settings and define how old log entries should be handled. If you choose the option never to overwrite events, normal users might receive messages intended for an administrator. The message might report that the event file is full and must be saved by an administrator. When this happens, the user usually informs the administrator so that such messages will be dealt with appropriately.
The Control Panel provides a comprehensive set of specialized administration tools for operating system configuration, applications, and Windows services. The main Control Panel and its Administration window contain a number of icons. Each icon is assigned to a tool for setting different parameters. The tools in the Administration window are identical with the tools under Start\Administration.
How do you display and launch the Control Panel tools? This depends on the configuration of the Start menu. You can choose the new Category View or the familiar Classic View. In the new Category View menu, the Control Panel is displayed as a link to a separate window containing the Control Panel tools. Within this window, the tools are displayed in the Classic View or the more tightly structured Category View.
Under the Start menu properties, you can also completely fade out the Control Panel or display it as a complete menu. In the latter case, all Control Panel tools can be invoked directly from the Start menu—there is no Category View.
If you selected the Classic View of the Start menu, you access the Control Panel via Start\Settings\Control Panel. The expanded Start menu options allow you to choose whether the Control Panel tools are launched directly from the Start menu or in a separate window.
| Tip |
If you would rather not configure the Start menu bar for Control Panel access, you can just as easily open it from Explorer. It is always located under Desktop\My Computer\Control Panel. |
Some tools are used for system-wide settings by an administrator, and some are intended for user-specific settings. You will find not only the standard icons for Windows Server 2003 tools in the Control Panel. Some system or application programs that are installed later add their own icons.
Even the standard Control Panel tools offer so many settings that to describe each would go well beyond the scope of this book. Some tools, however, allow the modification of parameters that are important to a terminal server runtime system. These tools and their options are the focus of the following section.
If you select the System tool under Control Panel, a dialog pops up in which you can select the view and modify system properties. You have to be in a user group with administrator privileges to take advantage of this option. The dialog has the following tabs: General, Computer Name, Hardware, Advanced, Automatic Updates, and Remote.
The first three tabs apply to general settings and are not particularly significant for terminal servers. The General tab offers information on the system, the registered user (including the license key), and the computer. The Computer Name tab allows you to modify the computer description, name, and working group or domain. The Hardware tab enables you to install new hardware, change device driver properties, and set up different hardware profiles. The latter option is not particularly relevant to terminal servers.
The Advanced tab, however, is extremely relevant. It contains options for adjusting system performance and user profiles, and for system start and recovery.
Clicking the Settings button under Performance opens a new window named Performance Options that has two tabs. The first is the Visual Effects tab, and it allows you to change settings relevant for desktop display. The default setting on a terminal server is automatic selection of the optimum setting. This ensures the performance-friendly display of graphics elements, which means that some visual effects are no longer used, such as animation, shadowing, or displaying window contents while dragging.
If an authorized user changes the default setting, RDP user sessions can significantly burden the terminal server’s resources with visual effects. For this reason, it might be practical to predefine the option for optimum performance on terminal servers or allow only a few user-defined options (for example, through Group Policies). Generally, the default setting is suitable for most terminal server environments.
The second tab in the Performance Options window is named Advanced, and it lets you define processor time, memory use, and virtual memory. The processor resources on a terminal server should be optimized for programs, not for background services. Background services mainly play a key role on back-end servers (for example, database or e-mail servers) and should therefore have priority there.
| Important |
A terminal server’s primary task is executing as many end-user programs as possible. Optimizing processor resources for programs involves both foreground and background applications. Therefore, this is the best setting to fulfill terminal server requirements. |
The question of the optimum setting for memory use has no easy answer. The Windows Server 2003 default setting of best performance of system cache favors the terminal server as the server platform. If the terminal server users work mostly with the same applications, a large cache is certainly advantageous because it provides faster access to already loaded data structures (for example, start screens or generally valid dialog windows).
By modifying the memory usage settings to optimize programs, the server assumes more of a workstation role. The programs run more quickly, but the entire system might reach its saturation point too soon because the data structures are not sufficiently reused. Comprehensive testing is needed to determine the best setting because it clearly depends on the combination of installed applications.
The Change button in this window opens the dialog for setting virtual memory. The initial and maximum size of the swap file and its physical location on the local hard drive are configured here. The swap file should not be limited to one partition because it can extend over several partitions or even hard drives. For the best results, these drives should each have their own channels on the hard-drive controller. This, in combination with a sizable initial swap file, increases system performance. To avoid dynamic growth in swap-file size, the start and end size should always match in a terminal server environment. These settings are not the same after installation, so they require manual adjustment.
After a standard installation, the predefined initial swap-file size for the virtual memory is about 1.5 times greater than the physical memory. The maximum size is approximately triple for physical memory. It is recommended that you set both the initial and maximum swap-file size to twice the size of the physical memory. For servers with substantial physical memory (greater than 2 GB), you may reduce this factor to 1.5. Increasing the file size is not the best approach for productive environments. So much hard-drive maneuvering is needed to access swap that is equal in size to physical memory that the server cannot keep up. Only thorough testing in a concrete target environment will reveal the optimum swap-file size.
The next setting on the Advanced tab is User profiles. Click the Settings button to open a new window. This is where individual user session profiles are managed. (See also later sections in this chapter.) All changes to user profiles must be made in this window. Manually copying, deleting, or moving profile directories in Explorer is not recommended.
The Change Type button allows you to assign either the local or the server- based profile to users logging on to this computer. A server-based user profile permits users to log on to other computers using the stored profile. This option is essential for terminal server farms. However, it is recommended that you implement this option under user administration by entering a terminal server profile or by configuring the profile path as a Group Policy.
The Settings button under Startup and Recovery allows administrators easy access to the start options in the Boot.ini file. Furthermore, the administrator can configure the system response to a STOP state, that is, a blue screen. By default, terminal servers automatically reboot in the event of a system error. If a system crash does not involve a hardware failure, the server will be back up relatively quickly. Debug information should be confined to a small memory dump or a kernel memory dump because a full memory dump would take up more hard-drive space than the additional data is worth. Therefore, this option is reserved for troubleshooting under the guidance of experienced support staff.
| Note |
If you would like to save a full memory dump in the event of a system error, you need sufficient space on the partition with the %SystemRoot% folder. Even if the final target of the backup file is elsewhere, it will be generated on the system partition first. |
The Environment variables button on the Advanced tab of the system tool allows you to modify the environment variables for the entire system and the current user. Only an administrator can add, change, or delete system-wide environment variables.
The Error reporting button automatically reports software errors to Microsoft. This option helps improve future products. Of course, you can disable this option as well.
Now that our extensive tour of the Advanced tab is complete, let us advance to the simpler Automatic Updates tab. This tab has no specific relevance to terminal servers; it ensures that the computer is kept up to date, if required. If you enable this option, you have the following choices for downloading and installing Windows update software:
Notification before each download and each installation
Automatic download and notification before installation
Automatic download and installation according to a preset schedule
| Tip |
Automatic update should not be activated for terminal servers because unmonitored software installations might be performed when the system is not in installation mode. (See Chapter 5.) |
Finally, the Remote tab is directly tied to terminal server functions. In this tab, you can enable or disable remote control for support tasks and access over remote desktop connections.
The Add or Remove Programs tool on the Control Panel is a convenient and powerful means of installing software. The Add New Programs button is used for this purpose. On a terminal server, the software tool changes the system environment to a special installation mode. After the installation is complete, the system is reset to application mode. (See Chapter 5.)
You can also set the different modes at the command line, a fact frequently overlooked by administrators and resulting in massive disruptions in the runtime behavior of the terminal server and its applications.